Security Testing Masterclass: Web, API and Mobile Application Security- Live Training
(Web, API & Mobile Security with Burp Suite, Vooki, Nmap, Zenmap, OWASP Juice Shop, WebGoat, Yazhini, Dex2Jar, JD-GUI, Snyk & More)
This course introduces participants to OWASP security concepts associated with REST APIs, SOAP APIs & Web applications. This is a foundation course & we encourage you to take this skill upgrade if you are a beginner in security world. This course uses vulnerable REST APIs, SOAP APIs & Web applications to demonstrate, identify security vulnerabilities as per OWASP top#10 standards.
About the Instructor:
| Kiran is an ITIL qualified Full Stack SDET specialist, Corporate Trainer and Consultant with over 19 years of experience in leading & delivering corporate training with tangible direction to IT professionals by imparting white-box knowledge in Software Testing, Security Testing, Test Automation, Test Practices & Competencies, Corporate Trainings & TCoE Delivery.
We cannot be good at something unless we like it and have fun doing it. The approach I take in my training sessions is to get the participants excited about technology and make it entertaining. I would like to consider myself an “Entertrainer”. → Successfully trained 6000+ employees across 500+ corporate giants & is still counting → Has been a trainer for both in-house as well as public, corporate programs and has streamlined the development of training material and training process for QA related areas, across corporate clientele and contributing to bottom line customer satisfaction |
Sample Videos:
“Security Testing Masterclass: Web, API and Mobile Application Security”-Demo Video
Security Testing Masterclass: Web, API and Mobile Application Security”-Day 1 Video
Live Sessions Price:
For LIVE sessions – Offer price after discount is 149 USD 139 119 USD Or USD15000 INR 13000 INR 9900 Rupees.
OR
Demo Session:
23rd April @ 9 PM – 10 PM (IST) (Indian Timings)
23rd April @ 11:30 AM – 12:30 PM (EST) (U.S Timings)
23rd April @ 4:30 PM – 5:30 PM (BST) (UK Timings)
Class Schedule:
For Participants in India: Monday to Friday 9 PM – 10 PM (IST)
For Participants in the US: Monday to Friday 11:30 AM – 12:30 PM (EST)
For Participants in the UK: Monday to Friday 4:30 PM – 5:30 PM (BST)
Prerequisites:
Good understanding of:
- Websites and web browser
- Client Server architecture
- Web Services/APIs testing
- Basic knowledge of HTTP/HTTPS protocol
- Basic understanding of HTTP methods
- Basic understanding of functional testing
What student’s have to say about Trainer :
| Thank you, sir. I used to have a fear of security testing and had zero knowledge about it, but after completing this course, I feel much more confident and informed. – Shilpaborkar
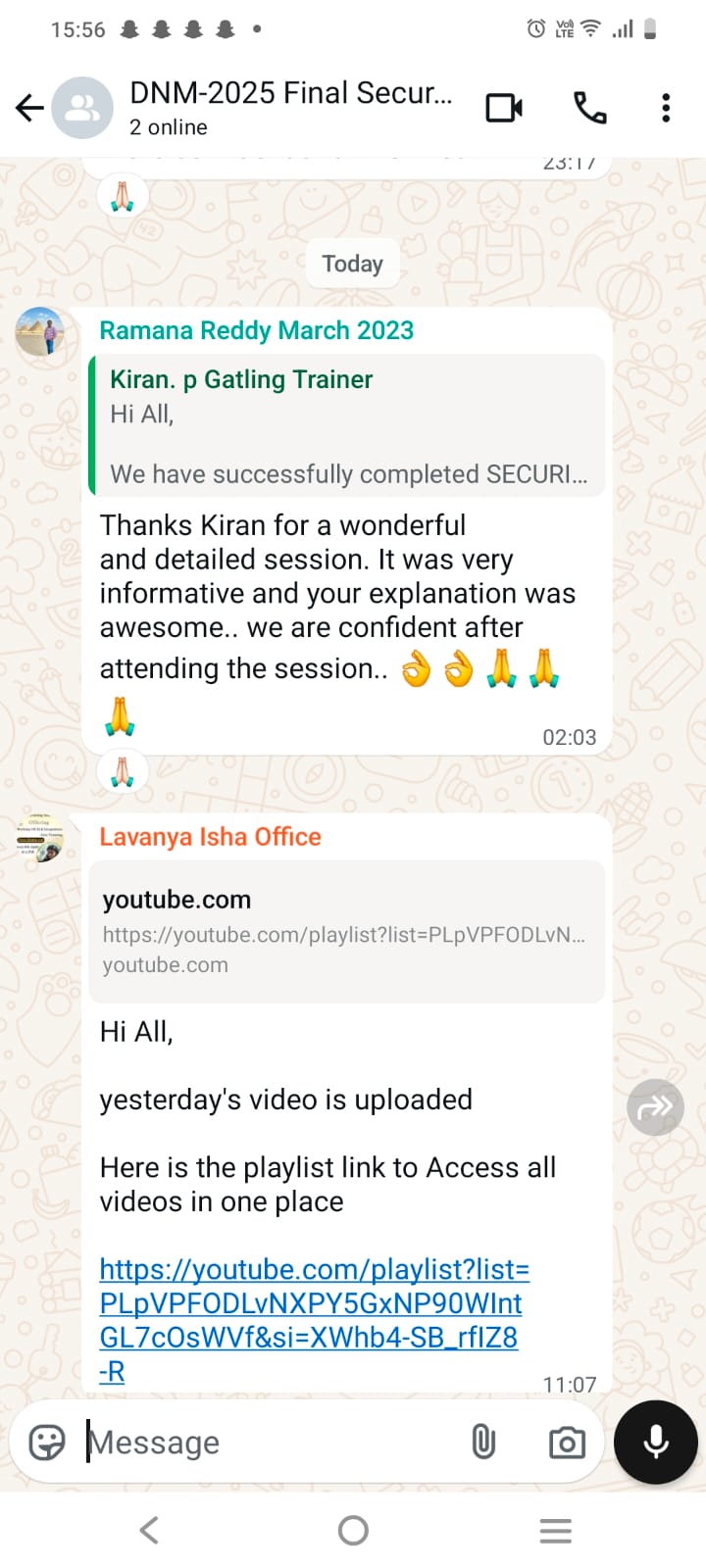
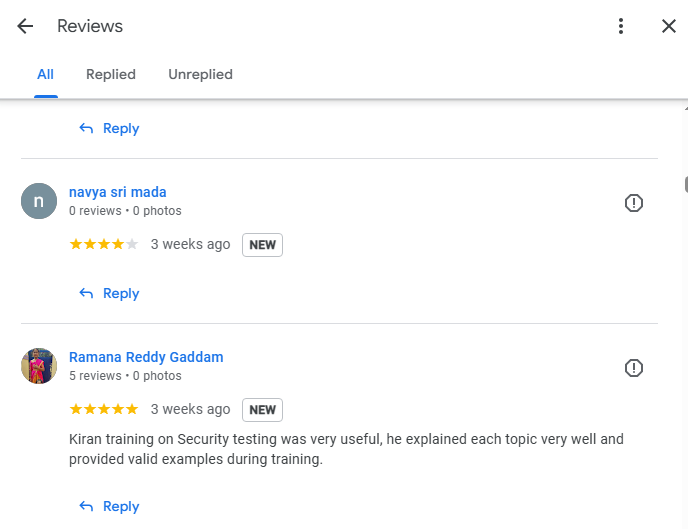
Thank you Kiran for the comprehensive sessions even from the very basics ! Enjoyed the sessions thoroughly !!! – zishan rabbani Kiran training on Security testing was very useful, he explained each topic very well and provided valid examples during training. – Ramana Reddy Gaddam Thanks Kiran for a wonderful and detailed session. It was very informative and your explanation was awesome.. we are confident after attending the session.. 👌👌🙏🙏🙏 – Ramana Reddy Easy to understand even difficult concepts, step by step explanation with real examples – Vick Excellent explanation from basics with clear examples. – Shan It is very good for learning and understanding in a simple and logical way. – Nick I appreciate your expertise on teaching the subject with so much clarity and depth. Thank you for being such a wonderful coach and guide. – Latha To the point explanation by instructor, Realtime examples also shared. learned alot through this course. – Kamala Thank you so much Kiran Sir for the wonder full explanation worth to watch,and you always proves that anybody can learn anything from scratch, if trained by good trainer like you. – Satish |
What will I Learn by the end of this course?
- By the end of this course, you will become a OWASP Security testing specialist:
- LO1 Understand OWASP top#10 vulnerabilities for Web applications & backend APIs
- LO2 You will get complete knowledge on REST API, SOAP API, Web applications, Android apks, & Port security testing
- LO3 In-depth understanding of exploiting OWASP vulnerabilities on vulnerable applications & APIs
- LO4 Learn how to generate security testing reports using Security testing tools
- LO5 Learn how to scan source code for OSS vulnerabilities & conduct reverse engineering of source code-Android apks
Salient Features:
- 30 Hours of Live Training along with recorded videos
- Lifetime access to the recorded videos
- Course Completion Certificate
Who can enroll in this course?
- Security enthusiasts
- Security professionals intending to upskill for compliance based penetration testing
Course syllabus:
CHAPTER 1: INTRODUCTION TO WEB CLIENT & SERVER, 3 TIER ARCHITECTURE AND API INTRODUCTION/ BASICS
- What is an API and the use of an API in an enterprise application along with API examples
- Introduction to data description formats wherever API calls are developed & consumed in an application
- Introduction to web application architecture
- Client & Server model
- HTTP & HTTPS protocols
- SSL & TLS protocols
- HTTP Request Headers
- HTTP Response Headers
- Request & Response Cookies
- Hand-shake process
- HTTP Methods/HTTP verbs
- Safe HTTP methods vs Unsafe HTTP methods
- GET
- POST
- PUT
- PATCH
- DELETE
- OPTIONS & HEAD
- Examples demonstration for HTTP request headers, HTTP response headers, HTTP response codes
- Practical example for demonstrating client & server architecture model
- Discussion on 3 layer architecture of an enterprise application i.e., front-end, back-end & server/database
CHAPTER 2: EVOLUTION OF API’S, TYPES OF API’S & EXAMPLES OF REST & SOAP API’S
- Introduction to API Architecture/Web-Services
- SOAP API (Simple object access protocol – Application Programming Interface) & WSDL
- REST API ( Representational State Transfer – Application Programming Interface)
- Definition of an API Syntax –> Understanding HTTP Method, Protocol, API URI, End points, Query Parameters, Resources, Request body, Authentication type, Request Headers, Request Cookies
CHAPTER 3: INTRODUCTION TO OWASP TOP#10 WEB & API VULNERABILITIES [HANDS-ON-EXERCISE]
- What is a Threat, Target, Cvss, Cve, Vulnerability Assessment Testing, Penetration Testing, Security testing
- Sensitive information disclosure
- Using vulnerable & outdated components
- Incorrectly configured & missing response headers
- Insecure design
- Open network ports detection
- Server-side missing validations
- Broken access control
- SQL injection
- Cross-site scripting css/xss injection
- Html injection
- Idor attacks
- Jwt tokens abuse
- Security misconfiguration
- Brute force attacks/ddos attacks
- Unrestricted access to sensitive business flows
- Broken object-level authorization
- Broken user authentication
- Broken object property level
CHAPTER 4: DOWNLOAD & SETUP OF VULNERABLE APPLICATIONS [HANDS-ON-EXERCISE]
- OWASP Juice Shop
- OWASP Web Goat
- Altoro mutual bank application
- Parabank soft application
- Acunetix Test PHP application
- Blazedemo Application
CHAPTER 5: PORT SCANNING USING NMAP/ZENMAP TOOL [HANDS-ON-EXERCISE]
- What is Nmap [Network Mapper] tool
- What are network ports used for
- Download & Installation of Nmap tool for CLI execution & Zenmap tool for UI execution
- Executing commands to discover open, filtered & closed ports and to detect OS and services version details
- Learn how to do different scans i.e., basic/aggressive/quick scan plus/ping scan/OS/multiple hosts/intense scan
CHAPTER 6: INTRODUCTION & INSTALLATION OF BURP SUITE-SECURITY TESTING DAST TOOL [HANDS-ON-EXERCISE]
- What is Burp Suite tool
- Installation of Burp Suite Community Edition
- Walk-through of Burp Suite features
- Understanding Burp Suite tool capabilities
CHAPTER 7: CONDUCTING PENETRATION TESTING USING BURP SUITE TOOL [HANDS-ON-EXERCISE]
- Learn how to setup Burp Suite environment
- Explore the Burp features : Proxy, Target, Intruder, Repeater, Decoder
- Download & Install Burp HTTPS certificate
- Using Burp in-built chromium browser to capture HTTP requests & intercept the same
- Capturing the http requests by configuring Burp Proxy, Burp Interceptor & Burp Repeater
- Learn how to intercept http requests and tamper responses to check server behavior
- How to forward, drop intercepted requests
- Sending the requests to Burp Intruder for brute force attacks using various payloads
- Hacking credentials using Burp Intruder
- Sending the requests to Burp Repeater to test repeatedly with various request tamperings
- Point-to-point attacks using Burp Repeater
- Learn how to encode or decode the request parameters using Burp Suite Decoder
- Visiting BApp store to install top rated plugins to aid in security testing [HACK BAR-PAYLOAD BUCKET, CONTENT TYPE CONVERTER, HTTP METHODS DISCLOSURE, JSON WEB TOKEN ATTACKER]
CHAPTER 8: REST APIs, SOAP APIs & WEB APPLICATION SECURITY TESTING USING VOOKI TOOL [HANDS-ON-EXERCISE]
- Introduction & Installation of Vooki tool
- Walk-through of Vooki tool UI features
- Testing APIs for OWASP top #10 techniques
- Learn how to scan an entire website [Basic Scan, Full Scan, Penetration test, Crawler]
- Learn how to use SSL scanner, understand Cryptography, Domain & Host scanner
- Detect & understand the vulnerabilities identified during the web application scan
- Generate HTML test report for security vulnerabilities found at web application scan
- Conducting full scan on REST APIs that uses GET, POST, PUT, PATCH, DELETE methods
- Conducting full scan on SOAP APIs
- Generate HTML test report for security vulnerabilities identified at API security scan
- Detect & understand the vulnerabilities identified during the APIs scan process
CHAPTER 9: ANDROID APPS SECURITY TESTING USING YAZHINI, DEX2JAR & JD-GUI-DAST TOOLS [HANDS-ON-EXERCISE]
- Introduction and Installation of Yazhini tool
- Installation of Dex2Jar, Java Decompiler
- Scanning the Android apk for vulnerabilities
- Conducting Full scan, Basic scan on apk
- Reverse engineering to check if APK can be deobfuscated to see original written code
- Generating the vulnerabilities test report for Android apk scan
CHAPTER 10: FINDING SOURCE CODE OSS VULNERABILITIES [OPEN SOURCE SOFTWARE] – SAST [HANDS-ON-EXERCISE]
- What is Snyk tool used for
- Sign up & Sign in to Snyk tool
- Adding your Github repo to Snyk project list
- Scanning the source code using Snyk scanner
- Running Snyk from CLI mode
- Understanding the vulnerability test report
How can I enroll for this course?
OR
For any other details, Call me or Whatsapp me on +91-9133190573
Live Sessions Price:
For LIVE sessions – Offer price after discount is 149 USD 139 119 USD Or USD15000 INR 13000 INR 9900 Rupees.
Sample Course Completion Certificate:
Your course completion certificate looks like this……

Typically, there is a one-day break following public sessions.
Important Note:
To maintain the quality of our training and ensure smooth progress for all learners, we do not allow batch repetition or switching between courses. Once you enroll in a batch, please make sure to attend the classes regularly as per the schedule. We kindly request you to plan your learning accordingly. Thank you for your support and understanding.
Reviews:
Course Features
- Lectures 78
- Quiz 0
- Duration 25 hours
- Skill level All levels
- Language English
- Students 1856
- Assessments Yes
Curriculum
- 10 Sections
- 78 Lessons
- 25 Hours
- CHAPTER 1: INTRODUCTION TO WEB CLIENT & SERVER ARCHITECTURE , 3 TIER ARCHITECTURE AND API INTRO7
- 1.1What is an API and the use of an API in an enterprise application along with API examples
- 1.2Introduction to data description formats wherever API calls are developed & consumed in an application
- 1.3Introduction to web application architecture
- 1.4Safe HTTP methods vs Unsafe HTTP methods
- 1.5Examples demonstration for HTTP request headers, HTTP response headers, HTTP response codes
- 1.6Practical example for demonstrating client & server architecture model
- 1.7Discussion on 3 layer architecture of an enterprise application i.e., front-end, back-end & server/database
- CHAPTER 2: EVOLUTION OF APIs, TYPES OF APIs & EXAMPLES OF REST & SOAP APIs2
- CHAPTER 3: INTRODUCTION TO OWASP TOP#10 WEB & API VULNERABILITIES [HANDS-ON-EXERCISE]19
- 3.1What is a Threat, Target, Cvss, Cve, Vulnerability Assessment Testing, Penetration Testing, Security testing
- 3.2Sensitive information disclosure
- 3.3Using vulnerable & outdated components
- 3.4Incorrectly configured & missing response headers
- 3.5Insecure design
- 3.6Open network ports detection
- 3.7Server-side missing validations
- 3.8Broken access control
- 3.9SQL injection
- 3.10Cross-site scripting css/xss injection
- 3.11Html injection
- 3.12Idor attacks
- 3.13Jwt tokens abuse
- 3.14Security misconfiguration
- 3.15Brute force attacks/ddos attacks
- 3.16Unrestricted access to sensitive business flows
- 3.17Broken object-level authorization
- 3.18Broken user authentication
- 3.19Broken object property level
- CHAPTER 4: DOWNLOAD & SETUP OF VULNERABLE APPLICATIONS [HANDS-ON-EXERCISE]6
- CHAPTER 5: PORT SCANNING USING NMAP/ZENMAP TOOL [HANDS-ON-EXERCISE]5
- 5.1What is Nmap [Network Mapper] tool
- 5.2What are network ports used for
- 5.3Download & Installation of Nmap tool for CLI execution & Zenmap tool for UI execution
- 5.4Executing commands to discover open, filtered & closed ports and to detect OS and services version details
- 5.5Learn how to do different scans i.e., basic/aggressive/quick scan plus/ping scan/OS/multiple hosts/intense scan
- CHAPTER 6: INTRODUCTION & INSTALLATION OF BURP SUITE-SECURITY TESTING DAST TOOL [HANDS-ON-EXERCISE]4
- CHAPTER 7: CONDUCTING PENETRATION TESTING USING BURP SUITE TOOL [HANDS-ON-EXERCISE]13
- 7.1Learn how to setup Burp Suite environment
- 7.2Explore the Burp features : Proxy, Target, Intruder, Repeater, Decoder
- 7.3Download & Install Burp HTTPS certificate
- 7.4Using Burp in-built chromium browser to capture HTTP requests & intercept the same
- 7.5Capturing the http requests by configuring Burp Proxy, Burp Interceptor & Burp Repeater
- 7.6Learn how to intercept http requests and tamper responses to check server behavior
- 7.7How to forward, drop intercepted requests
- 7.8Sending the requests to Burp Intruder for brute force attacks using various payloads
- 7.9Hacking credentials using Burp Intruder
- 7.10Sending the requests to Burp Repeater to test repeatedly with various request tamperings
- 7.11Point-to-point attacks using Burp Repeater
- 7.12Learn how to encode or decode the request parameters using Burp Suite Decoder
- 7.13Visiting BApp store to install top rated plugins to aid in security testing [HACK BAR-PAYLOAD BUCKET, CONTENT TYPE CONVERTER, HTTP METHODS DISCLOSURE, JSON WEB TOKEN ATTACKER]
- CHAPTER 8: REST APIs, SOAP APIs & WEB APPLICATION SECURITY TESTING USING VOOKI TOOL [HANDS-ON-EXERCISE]10
- 8.1Introduction & Installation of Vooki tool
- 8.2Walk-through of Vooki tool UI features
- 8.3Testing APIs for OWASP top #10 techniques
- 8.4Learn how to scan an entire website [Basic Scan, Full Scan, Penetration test, Crawler]
- 8.5Learn how to use SSL scanner, understand Cryptography, Domain & Host scanner
- 8.6Detect & understand the vulnerabilities identified during the web application scan
- 8.7Conducting full scan on REST APIs that uses GET, POST, PUT, PATCH, DELETE methods
- 8.8Conducting full scan on SOAP APIs
- 8.9Generate HTML test report for security vulnerabilities identified at API security scan
- 8.10Detect & understand the vulnerabilities identified during the APIs scan process
- CHAPTER 9: ANDROID APPS SECURITY TESTING USING YAZHINI, DEX2JAR & JD-GUI-DAST TOOLS [HANDS-ON-EXERCISE]6
- 9.1Introduction and Installation of Yazhini tool
- 9.2Installation of Dex2Jar, Java Decompiler
- 9.3Scanning the Android apk for vulnerabilities
- 9.4Conducting Full scan, Basic scan on apk
- 9.5Reverse engineering to check if APK can be deobfuscated to see original written code
- 9.6Generating the vulnerabilities test report for Android apk scan
- CHAPTER 10: FINDING SOURCE CODE OSS VULNERABILITIES [OPEN SOURCE SOFTWARE] – SAST [HANDS-ON-EXERCISE]6